Intro
Why do we want to have an active directory over 3 networks?
We want to keep the networks seperate to avoid an attacker being able to get from the client or DMZ network to be able to reach the active directory (AD)
Scope
- 3 networks to add to your virtualisation platform.
- 192.168.100.0/24 -> server network
- 10.0.0.0/8 -> client network
- 172.16.0.0/16 -> DMZ network
- NAT network
- a virtual router (opnsense in this example)
- a domain controller/dhcp server with 1 redundant server
- some clients
- a DMZ server
Setup
Set up an opnsense router. It's not difficult, just click next a couple times.
The networks
Assign the interfaces
Do not configure LAGGs nor VLAN's
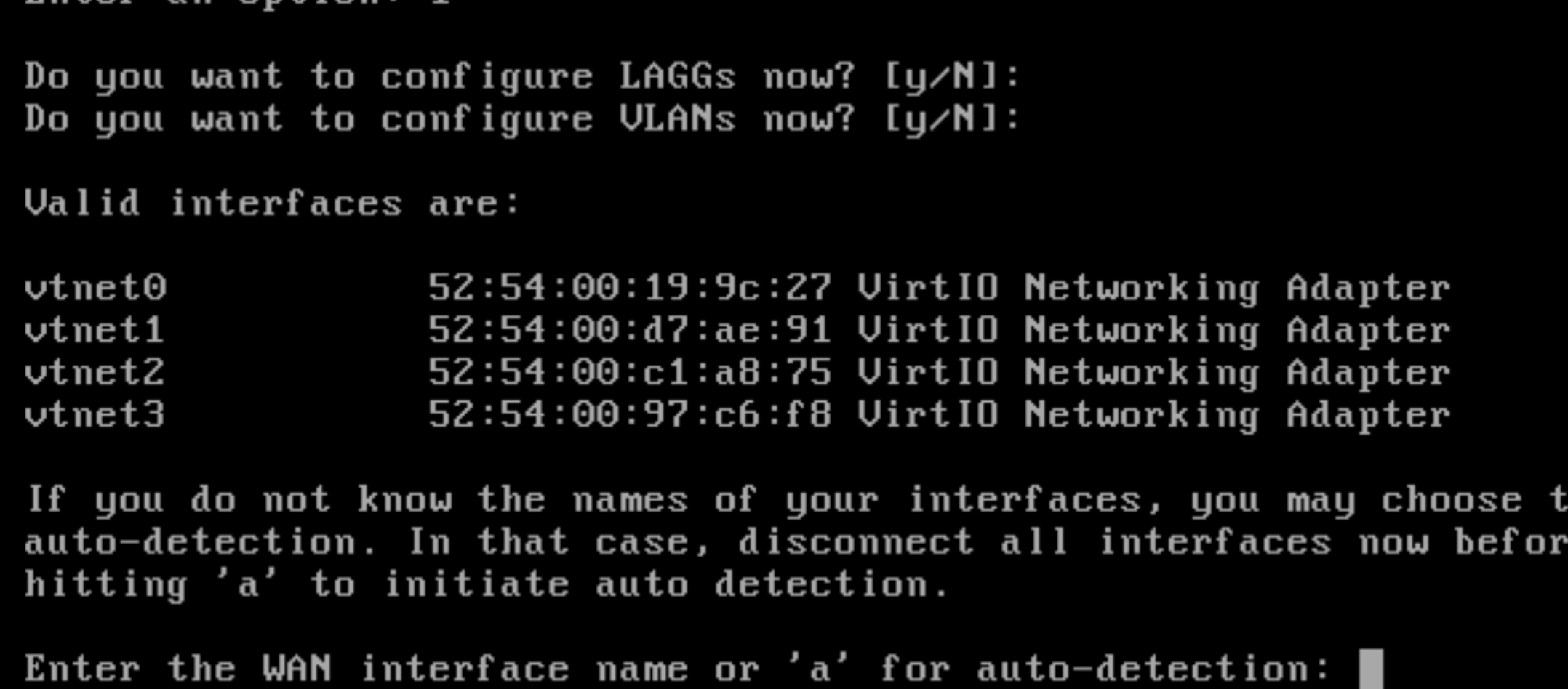
Look at the correct MAC address for the correct interface. This is your NAT or outgoing connection.
The rest are LAN's, but remember which one is which. We'll label them after they are set up.
Next, set up the IP's.
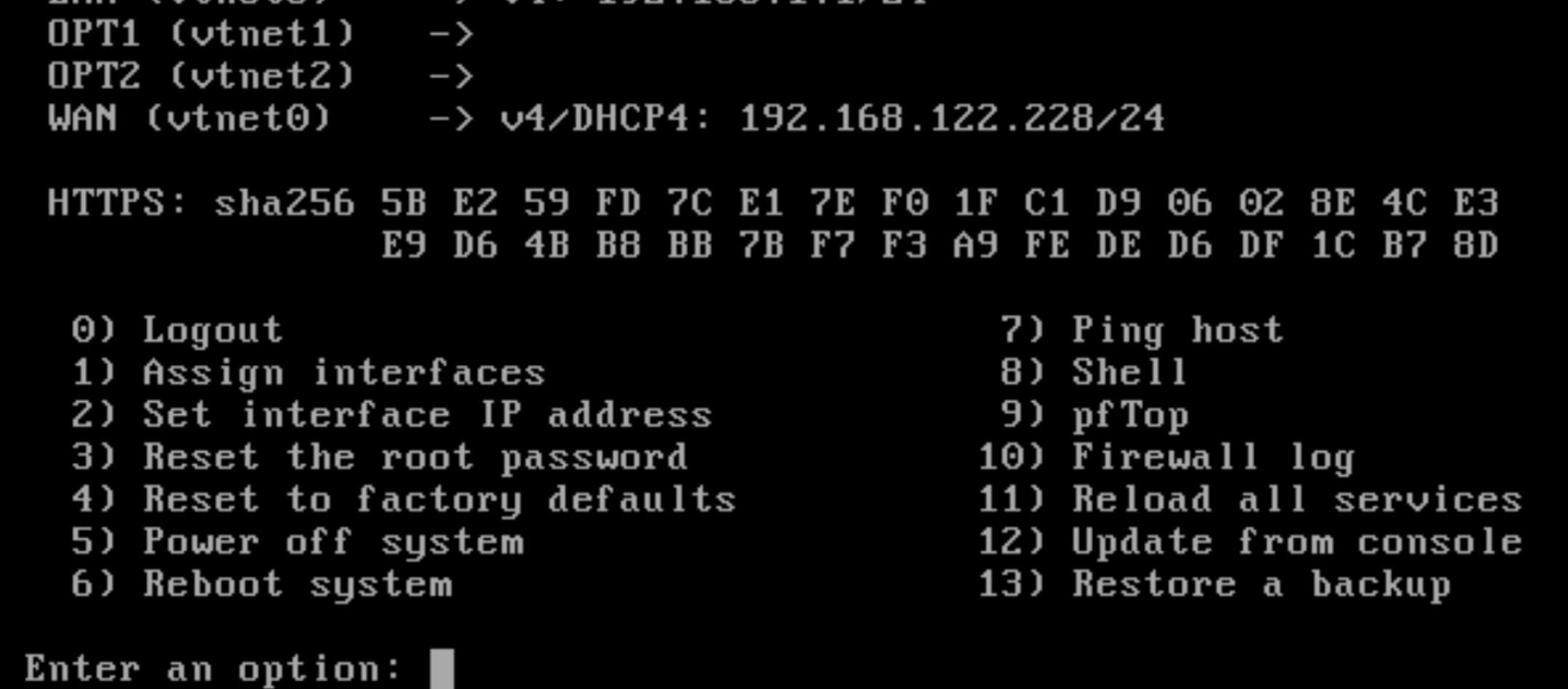
Fire up a client or a server in the client or server network and we'll label the networks.
Set up the correct gateway and browse to the router's IP and log in.
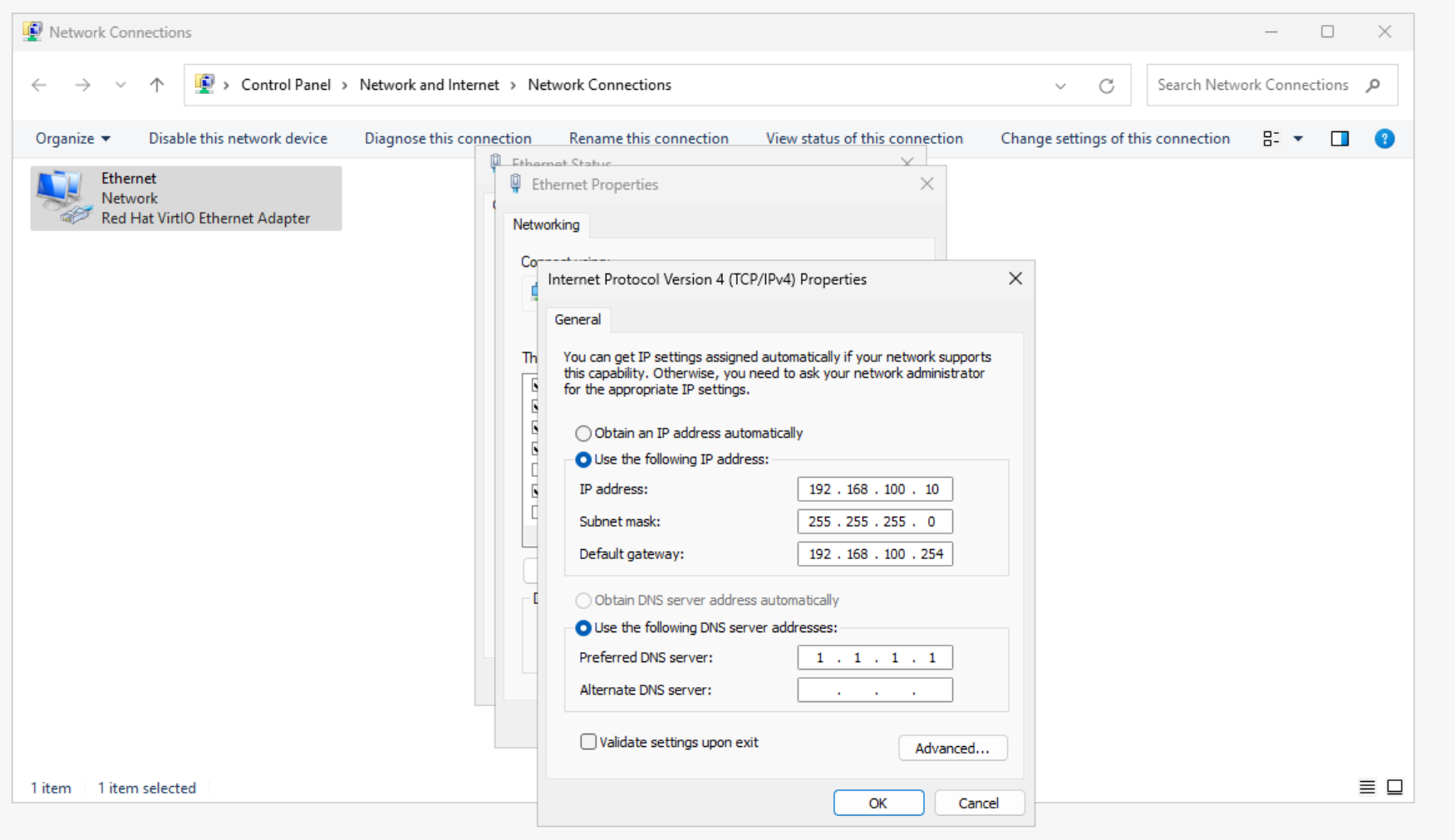
Walk through the configuration wizard.
Enter the description.
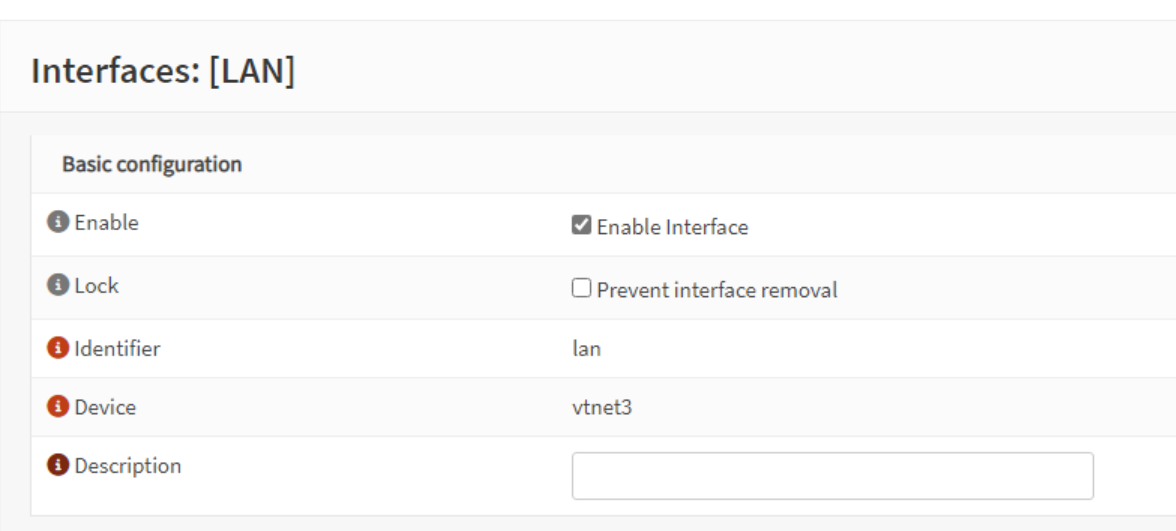
Now move to the firewall and let's set that one up. Navigate to the rules.
Let's start with the clients network.
Click the plus icon to add a rule
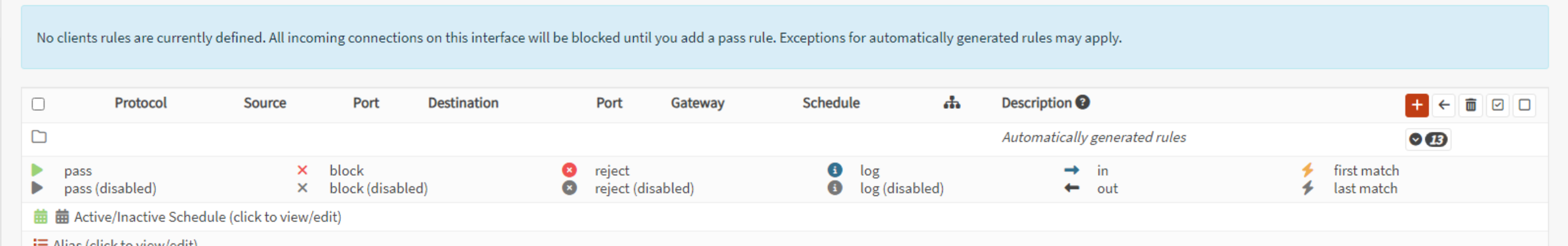
Specifiy a TCP/UDP pass rule and pass it to the NAT network.
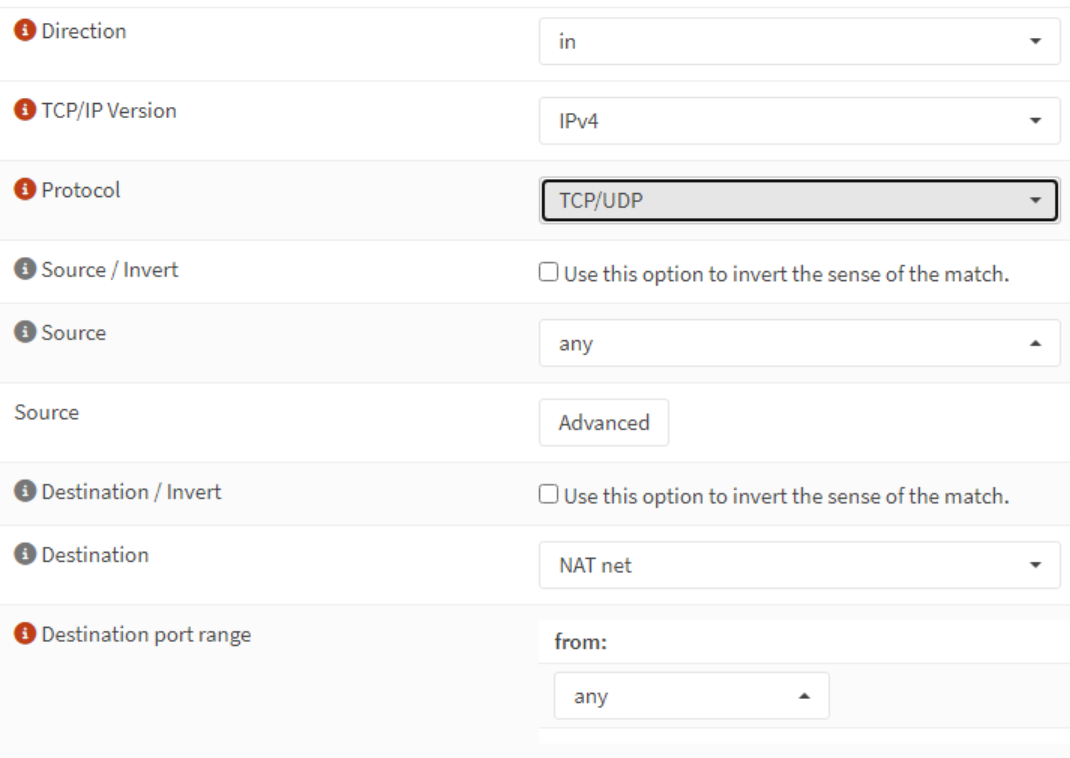
Let's move to the server, client and DMZ networks and apply the same settings.
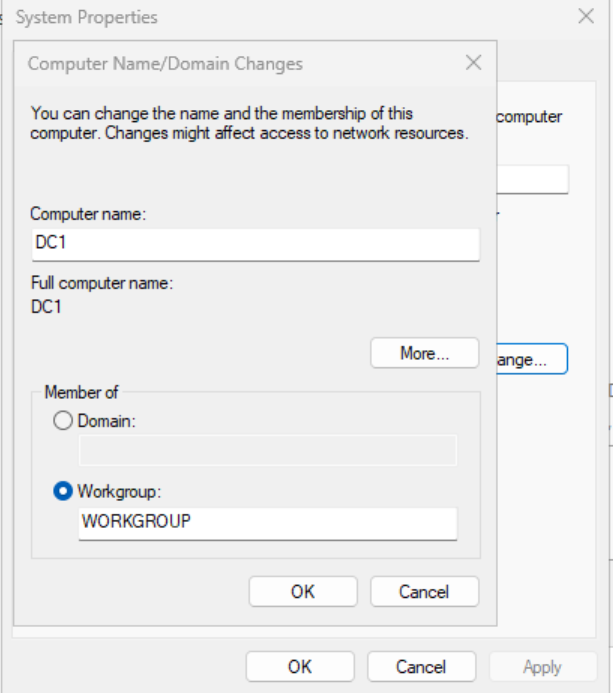
Change the name of the servers for easy identification.
Then move to the DHCRelay settings
And add these settings
The servers
Let's set up the AD on the first DC. I'm going to use powershell so everyone can follow.
Install-WindowsFeature -name AD-Domain-Services -IncludeManagementTools
Import-Module ADDSDeployment
Install-ADDSForest `
-CreateDnsDelegation:$false `
-DatabasePath "C:\WINDOWS\NTDS" `
-DomainMode "Win2025" `
-DomainName "idk.local" `
I also installed the DHCP role on the DC.
Join the second DC to the domain and add it to the AD. with the same steps.
The clients
If you configured everything correctly, the client should get an IP address from the server.
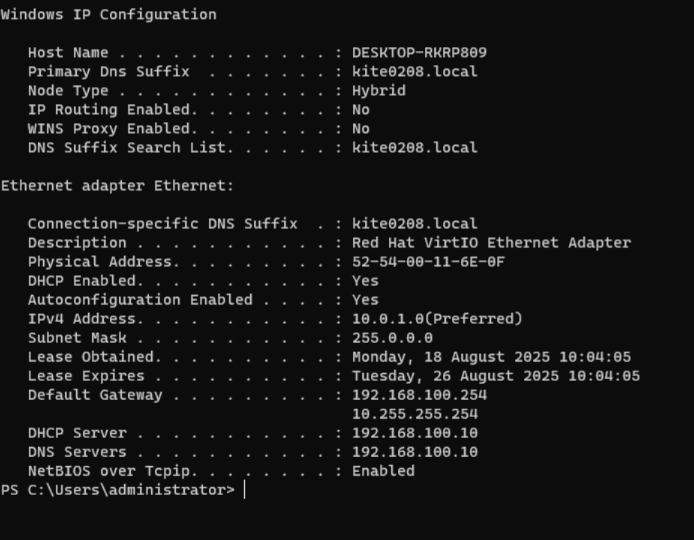
The DMZ
I installed apache2 on an ubuntu server to demonstrate the DMZ
https://youtu.be/XUb8kwJz_gc
Sources
https://learn.microsoft.com/en-us/powershell/module/microsoft.powershell.security/get-credential?view=powershell-7.5
https://activedirectorypro.com/install-ad-ds/